Why Businesses Can’t Afford to Ignore Protection—And How Xcitium Helps Stop Threats Cold
Most businesses still think hackers want to bust through the front gates—some dramatic breach that sets off every alarm. That’s not how it works. These days, they go through the side door. A forgotten laptop. A compromised password. An app update that didn’t get patched. One weak link, and they’re in.
That weak link is called an endpoint, and your business has dozens—if not hundreds—of them.
Small Doesn’t Mean Safe
If you run a business with 10 to 100 locations and a lean IT team, you’re exactly the kind of company that gets targeted. Smaller organizations are faster to compromise, slower to respond, and far more likely to be running a patchwork of tools, vendors, and outdated policies.
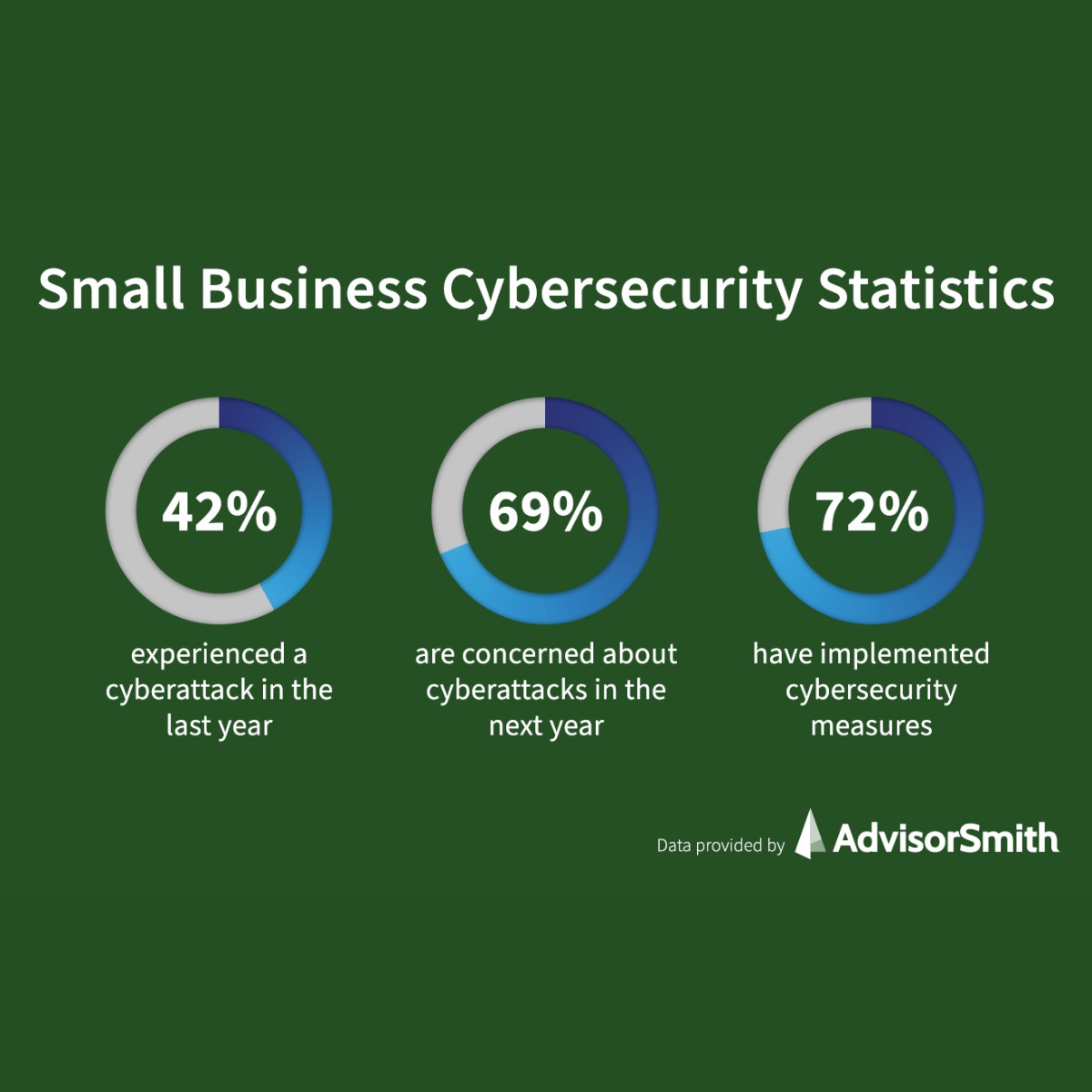

That’s not counting lost revenue, insurance spikes, or customer churn.
How Breaches Happen—And What They Really Cost
Let’s keep it simple:
- A team member clicks a phishing email.
- An app you use every day has an unpatched hole.
- A new vendor doesn’t follow your security practices.
Boom. You’ve got ransomware. Or worse, they’re already inside your system, quietly watching and copying files until it’s too late. Marriott shelled out $52 million after an endpoint breach exposed guest data. An Australian fund group was compromised because someone ignored an upgrade reminder. The point: you don’t need to be famous to get hit—you just need to be unprepared.
Meet Xcitium: Built to Prevent, Not Just Detect
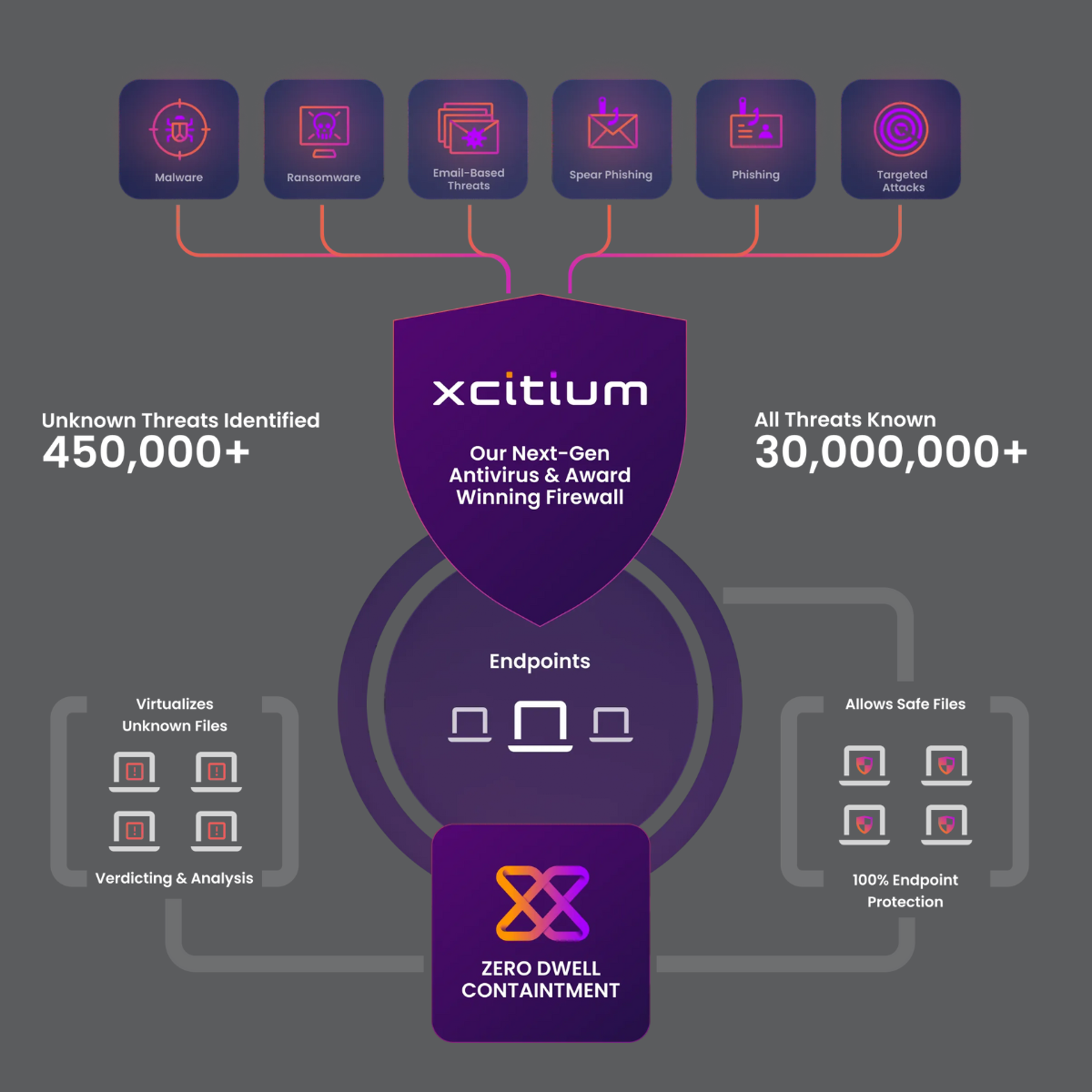
Most security tools react to threats. Xcitium blocks them before they get the chance to run.
Their patented ZeroDwell Containment™ Technology uses Kernel-level API Virtualization to instantly isolate unknown files, apps, and processes—so even if something suspicious shows up, it’s stuck in a safe zone where it can’t do damage.
Xcitium protects 4.5 million endpoints across 4,000+ companies, from healthcare to retail to finance.
What Xcitium Brings to the Table
- ZeroDwell Containment™: Catches threats before execution. No guesswork.
- EDR, MDR, XDR, RMM: All the tools you need, working together in one dashboard.
- Unlimited Incident Response: No retainers. No hidden fees. Just real help, when you need it.
- Built-in ITSM & Automation: Save time, boost efficiency, and reduce manual work.
- Free Risk Assessments: Understand your security gaps—before attackers do.
CNAPP Finds What Your Cloud Tools Miss
Most tools weren’t built for cloud-native environments. That’s why Xcitium developed its Cloud-Native Application Protection Platform (CNAPP). It’s designed to monitor your AWS, Azure, and Google Cloud environments in real time—and automatically lock down vulnerabilities and misconfigurations.
And if you think your cloud setup is too basic to matter, think again. Misconfigurations are the #1 cause of cloud breaches.
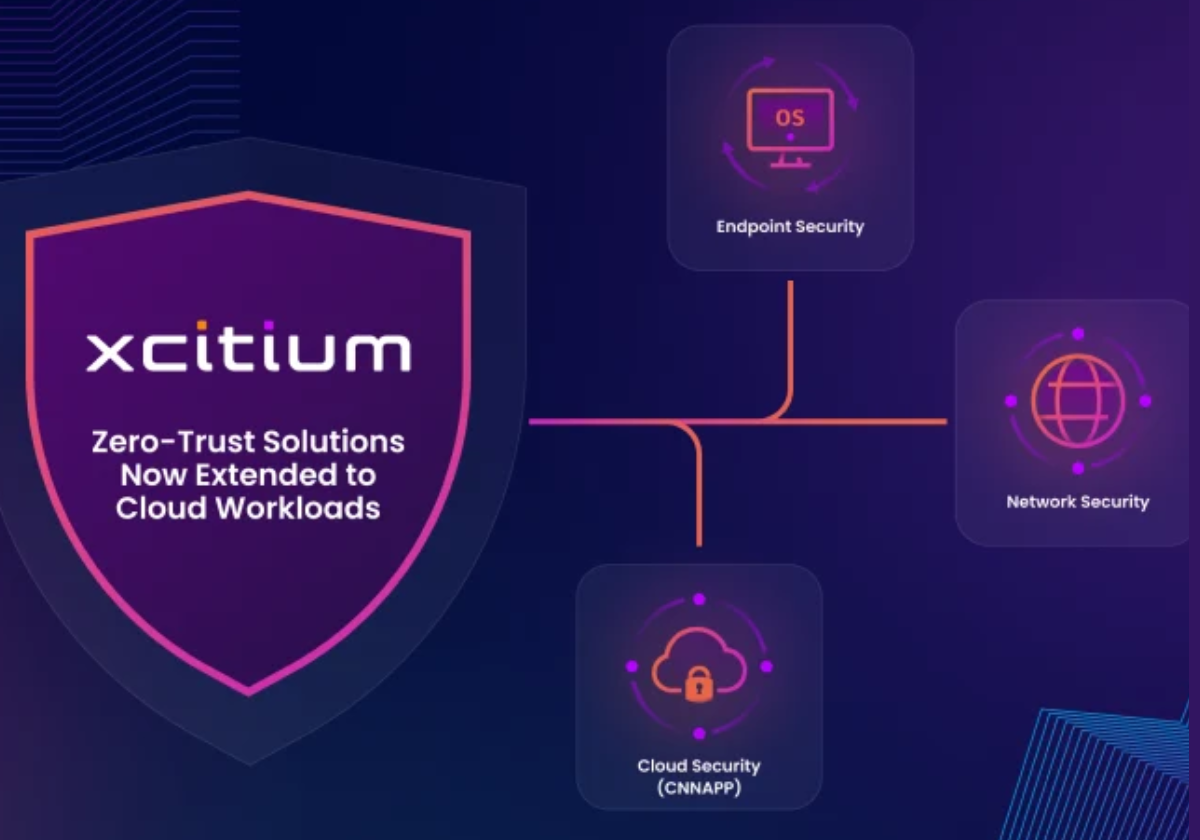

Xcitium CNAPP Does the Heavy Lifting
- Scans for compliance issues across SOC 2, HIPAA, NIST, and more.
- Identifies risks in containers, Kubernetes, APIs, and serverless functions.
- Offers free assessments that flag misconfigurations and offer fix-it guidance.
- Reduces the burden on your already stretched-thin IT team.
The CNAPP scan alone delivers full visibility into your cloud assets, IAM policies, and real-time workload behavior. It doesn’t just detect issues—it helps you fix them.
Where COMtuity Comes In
You don’t have to figure this out alone.
COMtuity is your tech translator and execution partner. We take the chaos of tools, platforms, and risks and simplify it down to a plan that actually works for your business.
We don’t just recommend Xcitium—we implement, manage, and optimize it with you. From the first scan to final rollout, we’re in the trenches with you.
Amanda’s Take
“Endpoint protection is about protecting your business from the stuff that can take you down. We’ve seen firsthand how the right tools—and the right team—can mean the difference between a minor alert and a full-blown disaster.”
— Amanda Cromar, COMtuity
Let’s Find Out Where You’re Vulnerable
Get a free endpoint risk assessment and take the first step toward real peace of mind. If you use cloud environments, we’ll also include a free CNAPP scan to uncover any hidden risks.
No sales pressure. Just clear answers and a path forward.

